Security CTF are an awesome way to learn new hacking skills and they are the best way to learn new skills and gain more experience in pentesting. There are two common types of CTFs: Jeopardy and Attack-Defence.
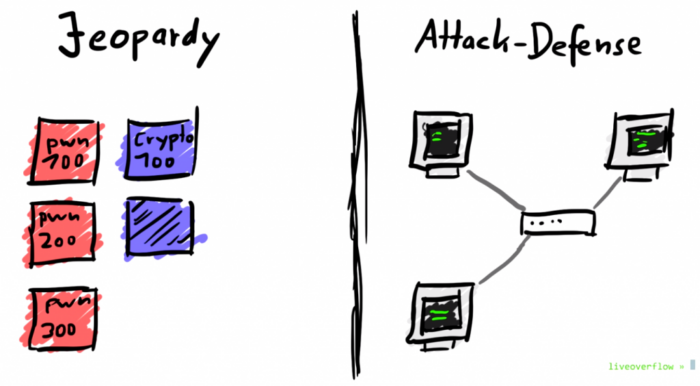
Jeopardy-style CTFs have a couple of questions (tasks) in a range of categories. For example, Web, Forensic, Crypto, Binary, and so on. An individual or team can gain some points for every solved task. More points for more complicated tasks usually. The next task in the chain can be opened only after some team solves the previous task. Then the game time is over the sum of points shows you a CTF winner.
Attack-Defence is another interesting kind of competition. Here every team has its own network(or only one host) with vulnerable services. Your team has time for patching your services and developing exploits usually. So, then organizers connect participants of the competition, and the wargame starts! You should protect your own services for defense points and hack opponents for attack points.
If you take a close look at the CTF world, Jeopardy-style CTF is more popular than the Attack-Defence style. If you want to enhance your skills then you must try CTFs which are happening all over the world. You can find the list of the CTF event at CTFTime.
In Nepal, we have been conducting NepHack, the only CTF event in Nepal for the past 3 years and we have seen progress on the participant and on the community. We have been organizing CTF to promote the security community in Nepal, to encourage security researchers, and eventually promoting the security sector in Nepal.

To know more about CTF, take a look at this video.
Here is a picture that will help you to get started.